[ad_1]
A cybersecurity agency yesterday reported {that a} group of infamous hackers from North Korea was in a position to steal $3 billion value of cryptocurrency from customers by devising a faux blockchain recreation. Kaspersky Lab mentioned that the Lazarus Group took benefit of a key vulnerability within the Google Chrome browser that allowed them to empty the crypto wallets of their victims.
Lazarus Group: $3 Billion Crypto Heist
It was reported that the North Korean hackers used the faux recreation to steal greater than $3 billion in cryptocurrency — an operation the group efficiently carried out inside a six-year interval, from 2016 to 2022.
The heist is the hostile consequence of Google’s failure to patch a vulnerability within the Chrome browser.
In the meantime, a blockchain detective conducting a separate investigation discovered that the Lazarus Group executed 25 hacking assaults, laundering $200 million value of crypto.
It additionally uncovered the existence of a community of builders in North Korea that works for “established” cryptocurrency initiatives. The community allegedly will get a month-to-month paycheck of $500,000.
The Doubtful Recreation Plan
Vasily Berdnikov and Boris Larin, analysts of Kaspersky Labs, mentioned that the Lazarus Group created a faux recreation known as DeTankZone or DeTankWar that revolves round Non-Fungible Tokens (NFTs) to siphon the crypto wallets of their victims.
The analysts revealed that the hackers made use of the zero-day vulnerability within the Chrome browser of their unscrupulous act.
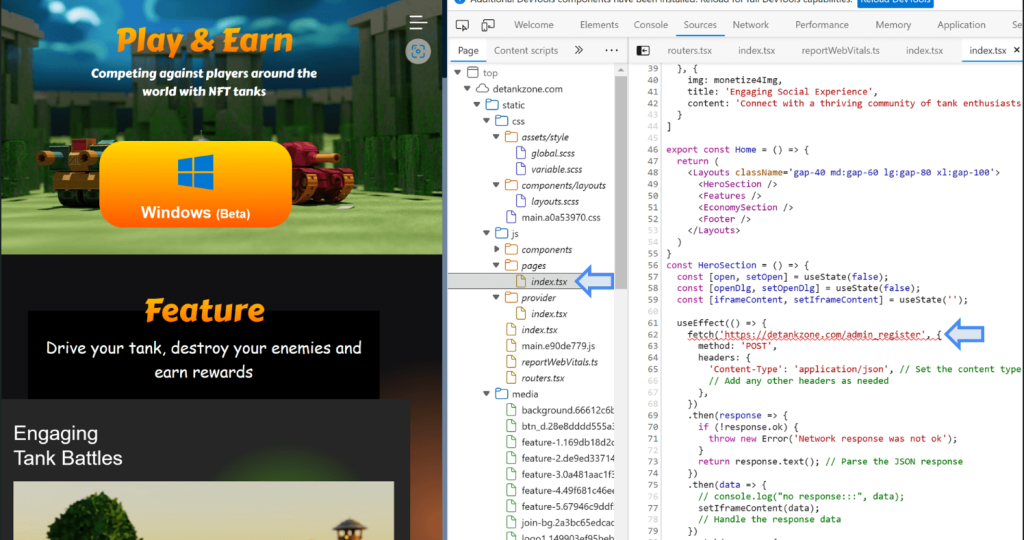
Web site look and the hidden exploit loader. Supply: Kaspersky Lab
Berdnikov and Larin defined that hackers used the faux recreation to steer their victims and led them to a malicious web site, which inject malware into their computer systems known as Manuscript.
With the usage of Manuscript, the hackers had been in a position to corrupt Chrome’s reminiscence, permitting them to acquire customers’ passwords, authentication tokens, and every part they wanted to steal the crypto of their unwitting victims.
12 Days To Remedy The Problem
Kaspersky Lab analysts found what the Lazarus Group was doing in Could. Berdnikov and Larin instantly relayed to Google the problem so the platform may repair the vulnerability.
Nevertheless, Google was unprepared to handle the zero-day vulnerability situation, taking them 12 days to repair the vulnerability.
Boris Larin, a principal safety skilled from Kaspersky Lab, mentioned that the notable effort invested by the hacker group within the mentioned hacking marketing campaign signifies that the group has an bold plan.
Larin famous that what the group has completed may need broader influence than beforehand thought.
The Lazarus Group is a reminder that the battle towards hackers continues. Chrome’s vulnerabilities emphasised that platforms ought to at all times make sure that their safety measures are up to date and be vigilant of cybersecurity threats.
Featured picture from Le Parisien, chart from TradingView
[ad_2]
Source link